The Civil War was the first warfare in taking advantage of the combination of electric telegraphy and cipher (though telegraphy had been used between headquarters in the Crimean War) (Friedman p.27).
It is well-known that the Federals employed a route transposition cipher devised by Anson Stager during the American Civil War. It developed from a very simple one written on a card into a complicated cipher book consisting of 40 pages of routes and code words. In the meantime, the scheme of indicating the route underwent several significant changes. The present article describes specifically what kind of changes Stager ciphers underwent, with worked out examples and also with references to the original cipher books recently made available online.
Table of Contents
Ciphers No. 6 and 7: Transition in the Meaning of Indicators
Ciphers No. 9, No. 10, and No. 12: Expanded Code and Irregular Routes
Cipher Management and Special Cipher for Grant
Ciphers No. 1 and No. 2: Commencement Words as Column Indicators
Ciphers No. 3, No. 4, No. 5: New Format
Other Route Transposition Ciphers
References (including links to extant copies of Civil War ciphers)
The First Battle of Bull Run (21 July 1861), the first major battle during the Civil War, ended in a defeat of the Union forces. The Confedrates also scored in communication and security.
During the battle, E.P. Alexander, founder of Confederate signal service, used signal flags to warn Nathan Evans that he was being outflanked, the first instance of such signaling over a long distance in the midst of a combat (Wikipedia; Brown p.44; Friedman p.34).
On 5 August, he wrote to his wife "Night before that I had some captured correspondence written in a cipher to unravel, & in fact have been at it occasionally ever since, & am going at it again as soon as I finish this. I have deciphered & read two letters that were brought in, but am stuck on a note book picked up on the field of battle, which I havnt yet found out any more about than that it was written by a confoundedly smart fellow." (Civil War Day by Day) This shows at least some of Union despatches were in a very simple cipher.
He appears to have obtained some reputation in codebreaking. On 16 August, he was sent a cipher letter captured at the battlefield of Bull Run from one officer, saying "At the suggestion of Genl. Longstreet I enclose herewith a cypher found on the battle field of the 21st. I have exhausted all my ingenuity in efforts to decypher it, and as it may contain something of interest I send it to you. If you should solve it will you allow me to trouble you to send me a copy of the translation." (Civil War Day by Day)
After the defeat in Bull Run, McClellan was called to Washington to reorganize the Union forces and he brought with him new ciphers devised by Anson Stager. (This is not to say that Stager was the first to use the scheme. A similar word transposition was employed by the Earl of Argyll in 1683, for which see another article.)
After the beginning of the war at Fort Sumter in April 1861, Anson Stager, general superintendent of Western Union Company, responded to the request of Governor of Ohio. Upon the Governor's solicitation, he prepared a cipher for communication with governors of Indiana and Illinois (Plum p.41).
Soon thereafter, he was called to General McClellan's home in Cincinnati, Ohio, where he devised a new cipher, similar to the one given to the governors. The small cipher (of which the first copy was given to the detective Allen C. Pinkerton for use in Kentucky) served McClellan in his campaign in western Virginia. (McClellan, then commander of the Department of the Ohio, was to be called by Lincoln in July 1861 to organize the Federal army.) It was also used by Anderson (Wikipedia) in Kentucky and Frémont (Wikipedia) further west.
Stager's cipher was a route transposition cipher, whereby words are reordered according to a predefined route.
Right after the beginning of hostilities in April 1861, the government called for telegraph operators for the defense of the Union (Bates p.14-15). Four best operators of the Pennsylvania Railroad Company were sent to Washington. These four, with one of them David Strouse as superintendent and another David H. Bates the author of a memoire used herein, formed the nucleus of the United States Military Telegraph Corps (USMTC), which would eventually grow to an organization of over 1500 members. (Bates p.25-27; Friedman p.31; Wikipedia) Technically, the USTMC was under Quartermaster General but for all practical purposes it was under the direct control of the Secretary of War (Firedman p.29).
Superintendent of the corps Strouse died in November 1861 and was succeeded by James R. Gilmore. The latter resigned and was succeeded by Thomas T. Eckert (Bates p.25, p.137), who had served as superintendent of the military telegraph for the Department of the Potomac during McClellan's Peninsula Campaign (March to July 1862) and whose papers are today beginning to be made available online. Eckert, in immediate charge of telegraph operations at Washington as chief of the War Department telegraph staff, became a principal assistant to Stager, who had been officially appointed as general manager of military telegraph lines in November 1861 (Bates p.31-32, 45, Plum p.147, Wikipedia). (Stager usually resided in Cleveland and mainly gave attention to matters in the West and Southwest (Bates p.34-35).)
According to W. R. Plum (p.60) (who was a cipher operator of General G.H. Thomas' headquarters late in the war (Plum vol.2 p.185 and in passim, Plum p.56, Friedman p.50, ASA p.71) and whose books provide primary information on Civil War ciphers), the Federal route transposition ciphers, originated by Stager, were developed by Stager but in no small degree by others such as T. T. Eckert, A. B. Chandler, D. Homer Bates, and Charles A. Tinker at the War Department. Tinker is said to have made "the arrangement" of the card form as shown below (Bates p.51). To these may be added General Grant's cipher operator S. H. Beckwith, whose contribution to Cipher No. 3 is mentioned below.
One example in the first of Stager ciphers is as follows (Plum p.45-46; ASA p.55).
To decipher this, the words in the ciphertext are written in 6+1=7 columns. The very first word of the telegram ("telegraph" in this case) indicates the number of lines ("8" in this case) beforehand. In each row, only the first six words are relevant, with the last word just inserted for confusion.
| (2)↓ | (4)↓ | (6)↓ | |||||
| 1 | 2 | 3 | 4 | 5 | 6 | ||
| 1 | the | have | be | not | I | hands | |
| 2 | right | hired | held | must | start | my | |
| 3 | to | an | responsible | Crittenden | to | at | |
| 4 | ascertain | engine | for | Colonel | desiring | demands | |
| 5 | the | to | success | by | not | reputation | |
| 6 | state | go | of | superseded | Crittenden | past | |
| 7 | of | up | this | being | Colonel | my | |
| 8 | the | road | division | since | advance | sir | |
| (4)↑ | (3)↑ | (1)↑ |
The words arranged thus are to be read by columns according to a predetermined route: first up the sixth column, then down the first, up the fifth, down the second, up the fourth, and down the third. The plaintext is as follows.
Since this cipher used 6 columns, it was called the "old six column" some years later (Plum p.59). It would be obvious that if the number of columns is fixed, the key ("telegraph") has no use, as pointed out in ASA, p.54, which would be the point of revision in Ciphers No. 6 and No. 7 below.
The whole cipher (written on the back of a small card) is as follows. (The routes were only orally communicated.)

The first column (1 Mail, 2 May, ...) lists words indicating the number of lines ("No. lines"), called "commencement words" because they are placed at the beginning of a telegram. The second column lists nonsense words to be inserted after every sixth word. Since these words should appear at fixed intervals, they may serve as check words (hence "check words"). But apparently, cipher operators did not stick to these words, as in the example above. The columns labelled "arbitrary words" are code words for some names.
Ciphers No. 6 and No. 7, very similar to the first one prepared for McClellan, were introduced within the year 1861 (ASA p.57). They were held by many in the west. In particular, they were used during General Buell's early operations in Kentucky and Tennessee (his command being from November 1861 to October 1862 (Wikipedia)) and Halleck's up to the occupation of Corinth (May 1862 (Wikipedia)). In the east, similar but different ciphers were used (Plum p.47).
In August 1862, a cipher operator Brooks was captured at Gallatin, Tennessee, a Federal outpost, during Colonel John H. Morgan's raid against the railroads and telegraphs, and these keys were abandoned (Plum p.47, p.275-277). Having said this, the example in Cipher No. 7 from 29 September 1862 below shows that it took at least a month to replace No. 7. (Before this, in May 1862, a novice operator John J. Wickham was captured by General Forrest at Murfreesboro but he could destroy his cipher key and all the dispatches before capture (Plum p.274).)
One significant change in No. 6 was that the commencement words now indicated the number of words in the message rather than the number of lines (mail: 6, may: 12, August: 18, etc.). This change may reflect a realization that the number of lines is irrelevant as long as the number of columns is fixed, though the compilers were not yet ready to simply abandon the indicator (ASA p.58).
Cipher No. 7 reverted to the indicator for the number of lines but made a significant change in the process of enciphering/deciphering, which made the indicator meaningful. This is now explained with the following example.
A telegram in Cipher No. 7 is as follows (Plum p.47, ASA p.58).
(At the time, most messages for Washington were addressed to Stager. The sender Drake is the cipher clerk. Real sender and recipient were written in the message in code names.)
To decipher this, the indicator "Austria" is now relevant. Since this indicates 9 lines, the recipient writes the words in columns of nine words according to the specified route as below, discarding every tenth word.
| (4)↓ | (6)↓ | (2)↓ | |||
| rapture | September | twenty | nine | 1862 | for |
| olden | ocean | I | have | received | your |
| orders | of | the | twenty | fourth | instant |
| requiring | me | to | turn | my | command |
| to | Camden | I | have | accordingly | turned |
| over | the | command | to | him, | and |
| in | further | obedience | to | your | instructions |
| I | shall | repair | to | Indianapolis | and |
| await | further | orders | alvord | pretty | rough |
| (1)↑ | (3)↑ | (5)↑ |
Supplying names represented in code, the following plaintext can be discerned by simply reading line by line from top to bottom.
(The next day, the same correspondents used Cipher No. 12, as noted below. Cipher No. 7 was abandoned because it was compromised in August (Plum p.47).)
It can be seen that the indicator is now relevant. The recipient has to know the number of lines (the number of words in a column) to write the words of the ciphertext column by column according to the route and the resulting text is read normally from left to right, whereas, in the previous version, the recipient writes the cipher words from left to right until the end of the cipher text (the number of words in a line being fixed) and the plaintext should be read according to the route.
In order to further see the change in the meaning of the indicator, the enciphering process of No. 7 is now compared with that of the original version.
In the example of Lander's telegram above, the sender prepares an 8-by-6 matrix (hence, the sender has to fix the number of lines before starting) and writes plaintext words according to the route (see above). Then, the words are copied line by line from top to bottom, inserting a null after every six words.
Now, in Buell's telegram in No. 7, the sender writes the plaintext with spacing between words so as to form 6 columns. (When finished, the number of lines is found to be 9.) The sender then copies the words in the order of the specified route, inserting a null after the end of every column.
The following is a facsimile of a "card form" of cipher used in 1861 (Bates p.51).

The instructions read as follows.
Its use ("Write 6 words in each line", "number of lines", "copying in the order of the route...") is similar to No. 7 above. (But it is not No. 7 at least because the code word "Alvord" does not represent Buell.)
It is noted that the number of columns "6" is handwritten, suggesting that the form was used with different numbers of columns. (Since there was yet no indication system, the number of columns was fixed, though it could be different from 6.)
In the code section, arbitrary words are printed, next to which words/phrases to be encoded could be written.
This template form allows users to choose their own route, assignment of indicators, and code names. (In this form, the number of lines is limited to 20. It was now realized the maximum 33 lines of the original version were too much for practice, as is clear from the instructions above.) This kind of printed template was also used in subsequent versions in enlarged form.
A cipher of an experimental nature is used in a dispatch of 16 August [1861] from Fitz John Porter to McClellan, which was deciphered by Assarpour and Boklan (2010). According to them, the recipient first writes the text in 8 lines (indicated by "telegraph" written in the margin) to obtain a 8-by-13 matrix and delete the word at the end of every row. [Alternatively, every 13th word might have been simply crossed out. This process allows detection of any words lost in transmission. That is, the deleted words are used as "check words."] Then, the remaining words are written according to a certain route column by column in a 16-by-6 matrix, with "16" indicated by "dress" at the beginning of the text and "6" being fixed.
Although this two-step scheme seems much more cumbersome than No. 7, the resulting plaintext seems too plausible to be wrong. Moreover, the route found out is one very easy to remember (as was that for the very first one above) and cannot be a coincidence: up the first, down the fourth, up the second, down the fifth, up the third, and down the sixth.
This dspatch of August 1861 shows that a scheme more complicated than No. 7 was in use right after McClellan brought Stager ciphers to Washington. It may have been one of trials before employing a more simplified Cipher No. 7. In particular, in this scheme, the "check words" appear to have been really used for check because they form an easy-to-identify orderly sequence: "fame", "faith", "fact", "face", "fade", "gild", "glass", ....
The present article adopts the year "1861". Although the description of the archives (which refers to Porter's telegram of 6 p.m. on this day in OR, vol.12, Part III, p.579) dates this 1862 because "the codes were not in general use in August 1861", Assarpour and Boklan (2010) corrects it to 1861 because by August 1862, more proper names should have been covered by a more advanced cipher like No. 12 (p.205-206). This alone, however, may not be conclusive because No. 7 was used as late as 29 September 1862.
August 1861 is just after the defeat of the First Battle of Bull Run on 21 July 1861 and at the time McClellan was endeavouring to reorganize the Union army. On the 16th, he was in Washington (McClellan's Own Story (Google) p.87).
On the other hand, the year 1862 may be excluded by the military situations. 16 August 1862 is shortly before the Second Battle of Bull Run. At the time, McClellan was rounding up his Peninsula Campaign and arrived at Williamsburg on the 18th (ibid. p.468). The destination "General G. B. McClellan / Washington City" is incompatible with this. Porter also arrived at Williamsburg on 16 August (OR, vol.12, Part III, p.595-596), pressed by McClellan to embark for northern Virginia. So, August 1862 does not match the events in the dispatch, which relate to the region further upstream of the Potomac from Washington, D.C. including Frederick, Waterford, Gum Spring, Loudon county, Jefferson county.
Huntington Library mssEC 38 is a cipher book attributed as "approximately 1863." Indeed, the names of major generals include some (C.C. Washburn, F.J. Herron) who obtained the rank as late as November 1862 (Wikipedia). S.B. Fairchild, whose name is written on the fly leaf, is one of telegraph operators who joined the Department of the Gulf apparently about the time General Nathaniel P. Banks took over command at New Orleans from General Butler in December 1862 (Plum vol.2, p.38).
The instructions are similar to those of the above card form.
(The numbers 6 and 10 are handwritten.)
There is no printed template for routes (as was the case for the very first one above) and routes, presumably orally communicated, are handwritten. Commencement words for 5 lines (Alfred, Adonis), 8 lines (Bertha, Barney), and 6 lines (Canada, Cora) are provided. Considering the number of columns is fixed, difference in the number of lines should have been irrelevant.
As with the early cipher card form, code words are printed and names of generals and places are handwritten. The code section has seven pages, each page containing 15 entries, each with two code words.
Ciphers No. 9, No. 10, and No. 12 are made on the basis of the same printed template, with a title "Cipher for Telegraphic Correspondence; arranged expressly for Military Operations, and for important Government despatches by Anson Stager" and a date "1861 & '62".
They have thus the same keys and arbitrary words, with only their meaning different. For example, the code word "Adam" or "Asia" meant "President Lincoln" in No. 9, "Gen. McClellan" in No. 10, and "Gen. Halleck" in No. 12 (Plum p.52). (Grant's cipherer Beckwith created a single code book by using black, blue, and red ink for No. 12, No. 9, and No. 10 (Plum p.52, Bates p.57, ASA p.66).)
Its body consisted of 25 pages, including a page of "TIME" section encompassing every hour and half hour of the day, 8 pages for routes for 3 to 10 lines, and 16 pages for arbitraries.
Compared with the previous versions, they had an expanded code section and some route patterns not by columns.
Cipher No. 12 was adopted in 1862 and was used until August 1864 (Plum p.48). It was discontinued because Stephen L. Robinson, a cipher operator accompanying General A.J. Smith on his march to deal with General Forrest (Wikipedia) was captured by guerillas in July 1864 (Plum p.49, vol.2, p.202-204).
Cipher No. 9 was introduced in January 1863, purely for precaution, for chief points and headquarters in the Western Departments (Plum p.52) (as well as Washington, in view of the examples below), while Cipher No. 12 was continued in general use (Plum p.52) (presumably, general use in the Western Departments, for reasons below). Cipher No. 10 followed a few months later.
Cipher No. 9 was not discontinued with the introduction of No. 10 but was to be replaced by No.1, which came into general use in February 1864 (Plum p.52).
The vocabulary in the arbitrary section may give an insight to the nature of these ciphers.
First, it appears that No. 12 was intended for the western theater. For one thing, governors of eastern states are absent in No. 12. The section of generals in No. 9 lists Winfield Scott, McClellan, Fremont, and Halleck in this order, followed by many others, while No. 12 lists only Halleck, Grant, Buell, Curtis, Wallace, McClernand in this order. The section of rivers and places of No. 12 also lack prominent names in the east that are found in No. 9.
The names of governors listed in Cipher No. 9 suggests it had been prepared after 19 April 1862 ("Edward S[a]lomon, Wis.", "Andy Johnson, Tenn.") and before 18 August 1862 ("Magoffin, Ky", "E.D. Morgan, N.Y."). (Lists of state governors of the United States) The names of Salomon, Johnson, and Magoffin also appearing in No. 12 suggest it was prepared in the same period. Thus, although Plum says No. 12 was the first of the series, No. 12 and No. 9 may have been both prepared in mid-1862 (though there is always a possibility that the compiler omitted to keep the entries up-to-date).
Further, the arrangement of the "miscellaneous" section under the arbitraries section of No. 9 looks as if it was augmented in several stages, while No. 12 has one integral "miscellaneous" section.
More dispatches in these ciphers should be gathered to discern exactly when these were in use.
The instructions read as follows.
The number of lines are now limited to 3 to 10 but the number of columns can be four to seven. For each number-line combination, a particular route and three commencement words are provided. The following is the page for the routes and keys for eight lines in Cipher No. 9, in which italicized words are handwritten.
| Morton Memphis Navy | 6 columns | Potts Porter Perry | 5 columns | Regular Rosecrans Run | 4 columns. |
Thus, the printed template for routes serve only one of three patterns. This inconvenience would be addressed in the next series (No. 1, No. 2).
In No. 9, the case of six lines is exceptional in that five, six, and seven columns (rather than four, five, and six for the others) are provided for. Moreover, the routes for five columns and six columns are specified not by columns, but by numbered positions. In principle, any random ordering is possible but it would have been inconvenient even for authentic users. Thus, the actually assigned routes employ one diagonal path but otherwise proceed by columns as usual.

In No. 12, irregular routes are assigned for the case of seven lines. In this case, the route is not rectangular. It may also be viewed to include squares to be skipped in the rectangle.

Stager got an idea of this scheme from a conversation in a train with a reformed gambler, who could remember the arrangement of cards by a sequence of numbers (Plum p.50). Anyway, such irregular routes were abandoned in the next series No. 1 and No. 2.
The code section was substantially enlarged. It encompassed names of civil and military officers on both sides, the states, rivers, and some common words. In total, Cipher No. 9 includes about 800 arbitraries (since most entries are given two arbitraries, the number of entries is about 400). It is remarkable that the printed words are somewhat out of alphabetical order, which would confuse the eavesdropper, while still manageable for authentic users (as pointed out in Friedman p.49).

One telegram in Cipher No.12 is as follows (Plum p.50, ASA p.62).
The recipient would find that "Regulars" (as well as "Rosecrans" and "run") indicates that there are nine lines and five columns, with the route: up the fourth, down the third, up the fifth, down the second, and up the first column. The recipients writes the received words (after the indicator "Regulars") according to this scheme, discarding one word after completing each column.
(For comparison, in Cipher No.9, "Regulars" (as well as "Rosecrans" and "run") indicate that there are eight lines and four columns, with the route: up the fourth, down the second, up the first, down the third column.)
| (4)↓ | (2)↓ | |||
| herald | September | thirty | 1862 | for |
| Adam | period | I | received | last |
| evening | your | dispatch | suspending | my |
| removal | from | command | out | of |
| a | sense | of | public | duty |
| I | shall | continue | to | discharge |
| the | duties | of | my | command |
| to | the | best | of | my |
| ability | until | otherwise | ordered | Arabia |
| (5)↑ | (1)↑ | (3)↑ |
Supplying the meaning of code words, the following plaintext is revealed.
It is noted that the telegram is sent the day after the example for Cipher No. 7 above, from the same sender to the same recipient on the same topic.
Kahn p.215 gives an example enciphered in No. 9. It is dated 1 June 1863.
Since "guard" indicates seven lines and five columns, a matrix is filled according to the specified route as follows.
| (2)↓ | (4)↓ | |||
| For | VENUS | Ludlow. | Richardson | and |
| Brown, | correspondents | of | the | Tribune, |
| WEYLAND | at | ODOR | are | detained |
| at | NEPTUNE | Please | ascertain | why |
| they | are | detained | and | get |
| them | off | if | you | can. |
| ADAM | ||||
| (1)↑ | (5)↑ | (3)↑ |
By restoring the code words, the following plaintext is obtained. (The last four words in the matrix are nulls to complete the rectangle.) It is noted that some names not in the code had to be written in clear.
The following is an example of Cipher No. 9, using an irregular route (Plum p.51, ASA p.65; though Plum discusses this under Cipher 12, he states the route is for No. 9 on p.372 and the route and code words match those of No. 9).
Girl's name "Clara" indicates the time (10:30 a.m.). Since "McClellan" indicates an irregular route for the case of six lines and six columns (see above), the recipient writes the received words according to the order of the numbers, discarding one letter when a square with "x" is reached.
| x | x | x | x | ||
| (6) for | (17) bear | (27) if | (36) blubber | (26) zebras | (16) have |
| (7) sufficiently | (5) occupied | (28) the | (35) enemy | (25) to | (15) render |
| (8) your | (18) line | (4) safe | (34) send | (24) all | (14) the |
| (9) forces | (19) you | (29) can | (3) spare | (23) to | (13) valley |
| (10) prentiss | (20) to | (30) operate | (33) on | (2) query | (12) world |
| (11) if | (21) he | (31) wafers | (32) towards | (22) chorus | (1) applause |
| x | x | x |
Supplying the meaning of code words, the plaintext is as follows.
It is noted that the code word for "advance" is "wafer" but the encipherer uses "wafers" for "advances." Similarly, "s" is supplied in code word "zebras" (Plum prints "movements" for "zebra" but the original shows the singular "movement"). For possessives ("Price's", "Sherman's"), the ending is left for the recipient to supply.
Gaddy p.94-97 gives another example in Cipher No. 9. It is a letter dated 16 October 1863 from Rosecrans to Burnside. It is enciphered in three parts. The first part is enciphered with the key word "Enemy", which indicates 10 lines and 6 columns. The subsequent parts are enciphered with the key words "Stanton" and "McDowell", respectively, both indicating an irregular route in a 6-by-6 matrix.
A despatch in this family of cipher from General Meade to General Couch dated 30 June 1863 (shortly before the Battle of Gettysburg) has been identified in 2014 by Maria Brady (The Blog of Gettysburg National Military Park; the original is in the preceding entry) to be one of the deciphered despatches (OR, vol.27, Part III, p.1084).
It is enciphered in five divisions. The message begins with "Wise", which indicates a 10-by-6 matrix and a route: down the third, up the sixth, down the first, up the fifth, down the fourth, and up the second. After this first message division comes an indicator "Halleck" indicating a 7-by-7 matrix for the next division, then "perry" [not "penny"] indicating 9-by-6, "Sibley" indicating 7-by-7, and "guard" indicating 8-by-6. These indicators and routes match those of Cipher No. 12.
Only a few code words are used: "Francis" for 11 am, "after" for General Couch, "Mohawk" for Washington, "Ida" for Baltimore, and "leghorn" for Philadelphia. Of these, those other than "after" match the printed key words of the template of Cipher No. 12 etc. but, except for "Francis", the meanings are different.
Notes are made here of cipherers because it may (or may not) be relevant in considering the nature of the despatch of Lincoln to Cameron, 15 July 1863 below.
In Meade's despatch above, as was common at the time, the actual sender and recipient as well as the date are enciphered in the message itself. Besides, the paper bears the names of the sender "G.W. Baldwin" and the recipient "O.W. Sees" and date "July 2nd, 1863." Maria Brady found out that Oliver W. Sees was chief of telegraph for Pennsylvania and at the time belonged to the staff of General Couch. Baldwin was at General Schenck's headquarters in Baltimore at the beginning of the Gettysburg Campaign (Plum vol.2, p.12) and somehow ended up in Meade's headquarters.
The telegraph operator at Meade's headquarters was A.H. Caldwell (who had been with Hooker before Meade replaced him (Plum vol.2, p.12)) but he left for Westminster without permission. Thus, the general was unable to send or read despatches in cipher at least for 3-4 July (the very days the Battle of Gettysburg was fought) (OR, vol.27, Part I, p.74, 78; Part III p.1088).
Baldwdin may have been called as relief on the absence of Caldwin, though conclusive evidence is yet to be sought.
The following is a message sent to General Meade the next day to the above (Friedman p.61-62; OR vol.27, Part III, p.474). The superficial sender is O.W. See. Friedman says this is in Cipher No.12. Again, the indicator and route match but the code words do not match those in the copy of Cipher No.12 in the Friedman Collection.
| (1)↓ | (3)↓ | (5)↓ | ||
| For | Parson (Meade). | I | shall | try |
| and | get | to | you | by |
| tomorrow | morning | a | reliable | gentleman |
| and | some | scouts | who | are |
| acquainted | with | a | country | you |
| wish | to | know | of. | Rebels |
| this | way | have | all | concentrated |
| in | direction | of | Gettysburg | and |
| Chambersburg. | I | occupy | Carlisle. | Signed |
| Optic (Couch). | Great | battle | very | soon. |
| (2)↑ | (4)↑ |
While ciphers were generally handled by cipher operators, occasionally generals and officers took it on themselves. General Lander's example is given above. The following correspondence further such exceptions.
In November 1862, General Grant had trouble in making his telegram in cipher understood by General Hamilton. In the winter of 1862-3, Captains Thoms and Thompson at Nashville under Rosecrans handled the cipher key (Plum p.59-60). Captain Thompson (as well as F.J. Porter above) had also a problem in his sense of security.
The following shows an officer's puzzlement in not being given the cipher.
It is imaginable that officers found it inconvenient that the cipher is kept by operators.
General Grant would be reprimanded for a similar transgression (see below). Later in the war, the ciphers were never to be handled by generals (Plum p.59; Friedman p.32). Still, the following shows one operator thought he might be given permission to hand his cipher to another operator.
In the fall of 1863, a dispatch in cipher from C.A. Dana, who was present at the Battle of Chickamauga (Wikipedia), was disclosed in the press. Dana suspected that it was improperly deciphered and leaked by the telegraph operator but the latter submitted that he had no key and he spoke of nothing but "surmise." Dana requested to Eckert for "a cipher whose meaning no operator can guess out." (OR, vol.30, Part I, p.208, 214).
(In the summer of 1863, there were similar incidents about the capture of Vicksburg but the leak was stopped by arrangements for delivery of messages from steamers to the telegraph manager (Plum p.329).)
Such incidents led to introduction of new ciphers (Gaddy p.99, Halleck to Grant, 22 January 1864).
(Gaddy p.98-101; Plum vol.2, pp.170-174; OR, vol.32, Part II, p.150, 159, 161, 323, 324)
It appears in late 1863, General Grant's headquarters was provided with a special "new and very complicated" (Halleck to Grant, 22 January 1864) cipher, which "differs in many respects from those formerly used" (Stager's notes of 21 January 1864), for communication with the War Department, while an "ordinary cipher" (presumably either of Ciphers No. 9, No. 10, and No. 12, to which was to be added Cipher No. 1 in February) was to be used with others (Halleck). In view of security, the cipher was to be communicated to no one but two individuals: one (Beckwith, cipher operator) in Grant's headquarters and the other in the War Department (Halleck). This resulted in an awkward incident over control of cipher.
When Grant stayed in Knoxville (from 31 December 1863 to 1 January 1864 for planning a campaign in east Tennessee (PUSG, vols. 9, 10)), he could not read Washington dispatches until he returned to his headquarters at Nashville (Gaddy p.101, Grant to Halleck, 4 February 1864; PSUG p.49, Grant to Halleck, 21 January 1864).
Unaware of the strict sense of security at the War Department, Grant simply remedied the inconvenience by directing Colonel Comstock of his staff to acquaint himself with the cipher. Although Beckwith wanted to consult Stager by telegraph, he could not resist Grant's order to disclose the cipher. (Grant to Halleck, 4 February 1864)
Stager telegraphed Beckwith that he must not divulge the cipher, upon which Grant protested to Halleck, General-in-Chief of the Union army, against this interference from Stager (Grant to Halleck, 20 January 1864). Unexpectedly, however, Grant received a reprimand from Halleck, who explained that the cipher should be "confided to no one else, not even to me or any member of my staff." (Halleck to Grant, 22 January 1864) and enclosed Stager's apologetic explanation that he did not think the request had been Grant's wish and that ciphers should be placed in the hands of experts because a great number of errors had been made by staff officers working ciphers (Stager's notes, 21 January 1864).
Since this special cipher was disclosed to Colonel Comstock, the Secretary of War Stanton directed another to be prepared in its place, which was "to be communicated to no one, no matter what his rank" (Halleck to Grant, 4 February 1864).
The nature of this special cipher is not known. The timing suggests No. 1 below but evidence ("differs in many respects from those formerly used", "no one but two individuals", etc.) is against such an identification.
The images of the original cipher books show that Ciphers No. 1 and No. 2 are both prepared with the same printed template as Cipher No. 9. The printed instructions of No. 9 are corrected by hand.
Cipher No. 2 was similar to Cipher No. 1, differing only in the meaning of arbitraries, key words specifying the number of columns and a route, and line indicators.
Cipher No. 1 came into general use in February 1864. Although Plum states it had been made in 1862, he might refer to the template. The entry of "C. A. Dana" (Wikipedia) (assistant secretary of war since January 1864 but a special investigating agent since 1862) following that of "Secretary of War" suggests it was made shortly before its use. The entries following thereto, "Maj. Gen. H.W. Halleck" ("General-in-Chief" in another copy), "General Grant", "Maj. Gen. Burnside", "Maj. Gen. Meade" in this order, also suggest the command hierarchy while Burnside led the Army of the Potomac after McClellan (November 1862 to January 1863) or after Meade replaced Hooker as commander of the Army of the Potomac (June 1863) but was still technically outranked by Burnside (Wikipedia). (No. 1 and No. 2 do not have a "governors" section.)
Cipher No. 1 might have been compromised when operators Pettit and Ludwig were captured when Athens, Alabama, was taken (Wikipedia) by General Forrest on 24 September 1864 (Plum p.52, vol.2, p.229-230). Although Plum says it was discarded at this time, there are at least two instances of its use as late as April 1865 as shown below (one of which can be found in vol.2 of Plum).
No. 1 was used for many important telegrams, while No. 2 (used at least in June 1864) was not so generally held as No. 1.
The main structural change in this series was that the commencement words now represent the number of columns rather than the number of lines. That is, the nine commencement words on each page are all for the same number of columns and one route. For example, in Cipher No. 1, "army" means five columns and a specific route. It would have been realized that it would be more convenient to classify the patterns by the number of columns rather than by the number of lines as in No. 9 etc. because a column route is defined for a specific number of columns, not lines.
For a specific number of columns, there may be several cases for the number of lines. For example, "dunce" and "snuff" meant one line; "charge" and "gold" meant ten lines, etc. The number of lines is indicated by the sum of two numbers indicated by two respective line indicators.
Page 3 (counting from the TIME page) for 6 columns in Cipher No. 1 had column indicators (now designated as "blind words" instead of "commencement words"): Driver, Dupont, Dunn, Enemy, Enlist, Engage, Forward, Foote, Forts, and the following line indicators.
| Address | 1 | Faith |
| Adjust | 2 | Favor |
| Answer | 3 | Confine |
| Appear | 4 | Bed |
| Appeal | 5 | Beef |
| Assume | 6 | Bend |
| Awake | 7 | Avail |
| Encamp | 8 | Active |
| Enroll | 9 | Absent | Enough | 10 | Accept |
While the printed template provides for up to seven columns, Cipher No. 1 defines routes with up to ten columns. So additional columns were added by hand. Occasionally, printed term "up" is written over with "down."
One feature of Cipher No. 2 different from No. 1 is that a figure is handwritten before each of the nine column indicators. Considering that the significance of the commencement words appears to have been discarded at some point (compare the two examples of No. 1 below), No. 2 may have undergone a change whereby the figures before the key words override the number of columns at the top of the page.
Irregular routes tried in No. 9 and No. 12 are not used in No. 1 and No. 2.
The code section of Cipher No. 1 included nearly nine hundred arbitrary words. For example, "Adam" meant Maine, "Arno" Arkansas, etc.; "apple" Fort Sumter, "animal" Fort Monroe, etc.; "Berlin" Red River, "Attica" Potomac, etc.; "Bologna" and seven others the President; "Bruno" and five others the Secretary of War, etc.; "black" or "blubber" City Point; "empress" or "embrace" Nashville, etc.; "hosanna" or "husband" Jeff. Davis, "hunter" or "happy" Gen. Lee, etc.; "Juno" and five others Gen. Grant, "lady" and three others Gen. Thomas (G.H.), etc.
Apart from these classified vocabulary, No. 1 covered phrases ("Peasant"/"Perfume" for by the way of, "Sligo"/"Stephen" for in the, "Yallow"/"Yawl" for encountered enemy in strong force) and ordinary words including verbs with inflections ("Putnam"/"Picket" for defeat-ed-ing), for which case "ed" or "ing" should be added to the arbitrary word in the ciphertext. Further, a handwritten page for numerals is appended.
Some increase in vocabulary with the same printed template was made possible by using some lines with two arbitraries (see the above image) for two words/phrases. For example, Cipher No. 9 assigns both "Adam" and "Asia" for "President of U.S." but Cipher No. 1 split the line into two by assigning these code words for "Maine" and "New Hampshire", respectively. On the other hand, some frequent words are now given three or more arbitrary words.
Now that not only military terms but also ordinary words and numerals are in the list, security relies more on the code (as ASA p.65 observes for No.9).
The copies of the Friedman Collection are based on printed templates different from those of the Huntington Library. These were preserved in the Adjutant General's Office and Friedman just happened to walk by when they were about to be burned as no longer of use (Friedman Papers). Of these, the copy of Cipher No. 1 has a printed addenda dated "September 9, 1864" so at least this was made later than its counterpart in the Huntington Library (which is called "the original" herein).
The printed templates of Ciphers No. 9 and No. 12 of the Friedman Collection are very much like those of the Huntington Library but not identical at least in that they have a title page simply with "WAR DEPARTMENT CIPHER NO. 9" or "WAR DEPARTMENT CIPHER NO. 12"; that the pagination is printed; and that "Message Division" in the route section is in italics.
The copy of Cipher No. 12 is appended with another entire code section, which is based on the same template as for No. 12 but has different assignment from that of either No. 9 or 12. This may be No. 10 but it lacks the route section.
The copy of Cipher No. 1 has printed not only the template but the whole of the TIME and routes sections (including the meaning of the code words/indicators). It also has printed the code words in the number appendix, the whole of which was handwritten in the original. The template for the code section has 29 lines per page, whereas that of the original has 26. Some additional code words handwritten in the margin in the original are printed (see Huntington Library, mssEC 43, p.11, "Baker ... Columbia ... Buffalo"; p.15, "Halifax ... Forrest ... Hospital"). On the other hand, some of the code words struck out in the original (e.g., "Apollo ... Altar" and "Alps ... Amber" for lines used for section headings) are omitted in the template.
This copy of Cipher No. 1 has a printed addenda dated "September 9, 1864", which has 16 pairs of code words printed and their meaning is handwritten. (It has one additional line (Hudson .... Handle) compared with the wholly handwritten addenda in one copy mssEC 44 in the Huntington Library and further two entries are handwritten.)
The copy of Cipher No. 2 is made based on this copy of Cipher No. 1. So, the printed TIME and route sections have been removed (the last page, the reverse side of which is the first page of the code section, was simply crossed out) and the template pages for Ciphers No. 9 and No. 12 are inserted instead. In the number appendix, all the printed code words of Cipher No. 1 are struck out and overwritten. (In the original, the whole of the number appendix is handwritten.) Moreover, the section for months (p.24) and some addenda (after p.25) not in the original are handwritten.
On the first page of the code section, two lines "Apollo ... Altar" and "Alps ... Amber" are handwritten in the margin because these lines were not printed in the copy of Cipher No. 1 as noted above.
It is not clear why the templates different from those for the original were made. At least for No. 1, it is understandable to prepare a printed template including handwritten addenda of September 1864 as well as the additional number section. But printing the specific route etc. caused some inconvenience in producing copies for No. 2.
The following is Plum's enciphering sheet in Cipher No. 1 (Friedman p.50). The ominous words in the margin "Lincoln", "shot" indicate 8 columns and 6 lines. More precisely, "Lincoln" indicates "8 columns" and the two other words "shot" and "small" indicate 4+2=6 lines.

The Huntington Library's project proposal ("Decoding the Civil War: Engaging the Public with 19th Century Technology & Cryptography through Crowdsourcing and Online Educational Modules" (pdf) p.5-7) includes detailed explanation of enciphering of a telegram from Lincoln to Godfrey Weitzel on 12 April 1865 (Collected Works of Abraham Lincoln).
It was enciphered in Cipher No. 1 with line indicators "next" and "news" (2+9=11 lines). However, the commencement word "Whats" does not match any of the nine words given in the corresponding page (for 10 columns). Considering that the term "commencement word" was changed to "blind word" by hand in Cipher No. 1, it may have been prescribed that the first word of the telegram is insignificant because the number of columns can be found on the page including those line indicators.
The following is the text after replacing some words (and punctuation) with arbitraries and others with irregular spelling (underlined).
Writing this with spacing between words so as to form columns, the following is obtained. (The last seven words are merely to fill the 11-by-10 matrix.)
| (8)↓ | (6)↓ | (1)↓ | (4)↓ | (10)↓ | (2)↓ | ||||
| Emma | Flood | Shelter | Weitzel | unity | I | have | seen | your | despatch |
| to | Paradise | Hardie | abe | out | the | matter | of | prayers | zebra |
| I | do | not | remember | hearing | prayers | spoken | of | while | I |
| was | in | galway | Pekin | but | I | have | no | doubt | you |
| have | acted | in | what | appeared | to | you | toby | the | spirit |
| and | temper | manifested | by | me | while | there | zodiac | Is | there |
| any | sign | Torch | Walnut | Legislature | coming | together | on | the | understanding |
| of | my | letter | to | you | Star | If | there | is | any |
| such | sign | in | form | me | what | it | is | Pedlar | if |
| there | is | no | such | sign | you | may | with | draw | the |
| offer | Yoke | Bologna | Why | dont | you | say | what | you | piloted |
| (3)↑ | (5)↑ | (9)↑ | (7)↑ |
Transcribing this according to the specified route, with an insignificant word inserted at the end of every column, gives a telegram to be transmitted.
The present author noticed the facsimile cipher dispatch printed in Plum vol.2 (p.287-289) is in Cipher No. 1 (see another article).
The following is an example enciphered with Cipher No. 2 (Plum p.53, ASA p.68).
"McDowell" indicates ten columns (A figure "8" is written before "McDowell" in the cipher book but, as noted above, it may indicate a later change in usage). The following "unsound" (2) and "vessel" (8) indicates ten lines. (Plum writes in his explanation "return" instead of "vessel" for indicating 8 lines. While ASA, p.69 inserts "return" by considering it was inadvertently dropped by Plum, it results in one word too many in the first column. The image of the original Cipher No. 2 shows "vessel" in the ciphertext, not "return" in Plum's explanation, is the correct word to indicate 8 lines.) So the words in the ciphertext are written in a 10-by-10 matrix according to a specified route.
| (2)↓ | (6)↓ | (4)↓ | (10)↓ | (8)↓ | |||||
| ginger | Luke | Morgan | mason | Russell | Baker | for | Cupid | happy | tulip |
| revenue | f | T | bale | of | violet | Peru | made | a | revenue |
| for | burning | the | sun | nay | side | spit | fork | proposes | to |
| leave | shreve | port | about | this | date | with | French | picked | assistants |
| to | byrne | and | quack | store | houses | boats | etc. | at | Egypt |
| brocade | and | Honduras | possibly | also | at | fraction | and | black | yacht |
| this | party | wilby | in | squad | of | Arnold | or | Austin | at |
| each | place | yardstick | they | pine | by | male | in | cipher | tulip |
| revenue | f | T | bale | was | former | like | law | your | |
| at | shreve | port | audit | period | he | is | about | Dayton | feat |
| (9)↑ | (5)↑ | (1)↑ | (7)↑ | (3)↑ |
(ASA, p.70 gives a helpful hint to this ciphertext by the editor, who, however, could not make sense of this ciphertext after a brief attempt. In addition to inserting the extra word "return" at the very beginning, the ciphertext of this edition drops no less than seven words after the first occurrence of "tulip" up to its next occurrence. The ciphertext "in about same", printed as "in about the same" in ASA, p.68, appears to be an error for "in a about same." The plaintext "T. F. Beal" given in Plum appears to be an error for "F. T. Beal", as correctly pointed out in ASA p.70.)
Since the message is long, the maximum 10-by-10 matrix could not contain the whole. The next words "volunteers resist surprise" indicates 9 columns and 2+7=9 lines. Again, filling a 9-by-9 matrix with the words of the remaining ciphertext according to the rule gives the following.
| (4)↓ | (2)↓ | (6)↓ | (8)↓ | |||||
| Clarke | or | Downing | inches | high | swallow | built | slender | slim |
| phased | freckled | swallow | Browne | hare | swallow | mouse | tash | stop |
| has | Ben | recently | cut | so | as | two | leave | scars |
| probably | on | Stephen | side | and | spit | topoph | head | above |
| and | a | little | behind | the | are | also | at | the |
| sulphur | of | nose | and | four | head | also | on | inside |
| of | Stephen | hand | spit | the | thum | yacht | he | spits |
| a | good | deal | while | conversing | all | wilby | in | poplar |
| close | sometimes | they | ware | pistils | Windham | mastiff | awful | hot |
| (1)↑ | (9)↑ | (5)↑ | (7)↑ | (3)↑ |
All that is left is to simply read line by line from top to bottom, by replacing code words with their plaintext equivalents. However, the task is made more difficult for an eavesdropper than in previous versions because of more extensive use of code words and use of irregular spelling. The latter's examples are "bale" for Beal, "sun nay" to "sunny", "byrne" for "burn", "wilby" for "will be", "male" for "mail", "law your" for "lawyer", "feat" for "feet", "phased" for "faced", "Browne" for "brown", "hare" for "hair", "mouse tash" for "mustache", "Ben" for "been", "two" for "to", "topoph" for "top of", "the are" for "the ear", "thum" for "thumb", "close" for "clothes", "ware" for "wear", "pistils" for "pistols". As can be seen, not only words are replaced with similar sounding words, word(s) are spelled with two words which may sound alike when pronounced not too slowly.
The plaintext is as follows. (The last three words in the second matrix are nulls to complete the rectangle.) It can be seen that even after the transposition is undone, decipherment is not easy without knowledge of the code words.
(The date line printed in Plum is "New Orleans, La., June 19, 1864. To Gen. Halleck, Washington, D.C.:" but the following is the direct decipherment: ginger(New Orleans) Luke(June) Morgan(19) mason(18) Russell(60) Baker(4) for Cupid (Gen. Halleck) happy (Washington) tulip(.). By the way, the plaintext counterpart for "Cupid" is "Maj. Genl H.W. Halleck" in one copy but "General in Chief" in another. Halleck became General in Chief on 23 July 1862.)
The following shows two pages from a handwritten copy of Cipher No. 2 made by General Grant's cipher operator Beckwith, who used to copy cipher books in his embellished handwriting (Bates p.56-58).
These pages provide for key words for nine columns and ten columns, respectively. Each page provides line indicators for the number of lines 1-15 (two for each number) and, at the bottom, column routes. This is Cipher No. 2, not No. 4 as Bates' description may suggest.

The new series of Ciphers No. 3, No. 4, and No. 5 were made on a new printed template, while Ciphers No. 1 and No. 2 had been made on the template for Ciphers No. 9, No. 10, and No. 12.
Ciphers No. 3, No. 4, and No. 5 differ chiefly in the specific routes and meaning of arbitraries.
The one-page TIME section of No. 9 is now expanded to four pages, encompassing time, day (1st, 2nd, ..., 31st), numerals (which had constituted a handwritten appendix page in No. 1), days of the week, year "1865" (for No. 4; also "1864" for No. 5), months, to which some handwritten arbitraries are added for punctuation.
There are 12 pages for routes, each containing a different route with different key words, to be described below.
The remaining 24 pages form the code section. The number of arbitraries now amounted to 1608 (exclusive of key words). (Plum p.56)
No direction was given in the book for precaution in case it was captured (Plum p.57), though it is not the case for the copies preserved in the Adjutant General's Office (see below).
Cipher No. 3, the first of the series, was introduced on 25 December 1864. Cipher No. 3 adopted many arbitrary words suggested by S.H. Beckwith belonging to General Grant's headquarters. Beckwith had carefully recorded words and expressions not yet covered by the arbitraries. Moreover, apparently he also selected such code words least likely to be garbled in transmission with American Morse code. (Plum p.55)
Cipher No. 3 was intended for use at headquarters of Generals Grant, Sherman, Thomas, Sheridan, and Canby but apparently it never reached the West. It was little used, if at all, after No. 4 was adopted. (Plum p.55-56)
Cipher No. 4 was sent on 23 March 1865 to cipherers at headquarters of the Military Department West of the Mississippi, Grant, Sherman, and Thomas. (Plum p.56) However, there is evidence that it had been used as early as 15 July 1863 (see below). Cipher No. 4 was used for Lincoln's despatches during his two weeks' stay at City Point and Richmond from 25 March to 8 April 1865(Bates p.58).
After the war, on 20 June 1865, Cipher No. 4 and all other ciphers were abandoned and Cipher No. 5 was sent out (Plum p.56).
Plum says Cipher No. 5 was sent out on 20 June 1865. The internal evidence indicates it was prepared shortly before this.
The section of governors (p.33) in the code section includes many who took office in January 1865 (Fenton, NY, Fletcher, MO, Oglesby, IL, Crapo, MI, Crawford, KS, and Swann, MD (the latter only took oath at this time and was to take office a year later according to Wikipedia)). Brownlow, TN, took office on 5 April 1865 and two provisional governors Johnston, GA, and Sharkey, MS, were appointed by President Jackson in June 1865. (Lists of state governors of the United States)
Moreover, on p.34, after three pairs of code words for "President of the U.S.", the code words "Ralph" and "Rape" are for "Andrew Johnson", who became president on 15 April 1865 after the assassination of Lincoln.
The above evidence seems strong enough and some conflicting evidence (governor William Cannon, DL, died on 1 March 1865 and Hahn, LA, resigned on 4 March 1865) may be just a result of an oversight.
Plum says Cipher No. 4 was sent out on 23 March 1865 and it is consistent with the entry "Lieut-Gen'l Grant" placed before Halleck (p.17). Grant obtained such a position in March 1864. (On the other hand, Cipher No. 5 lists generals in alphabetical order.)
In the number section, the only year given an entry is "1865" (p.4). (Cipher No. 5 provides for "1864" and "1865". Of course, this does not mean No. 5 was prepared in 1864.)
However, the example given in the directions on the backside of the title page matches Cipher No. 5 but not No. 4. This is difficult to explain unless No. 5 was the first of the series. A more serious counterevidence is Plum's record of use of Cipher No. 4 as early as 15 July 1863 (see below). Thus, the dating of preparation of Cipher No. 4 is yet an open question.
The route was indicated in a masked way. The entire page 7 of Cipher No. 4 is as follows (Plum p.57).
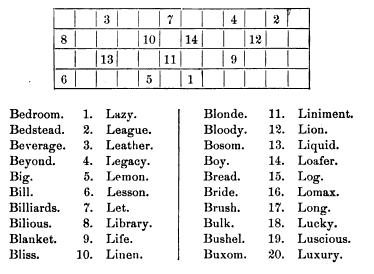
The corresponding page in Cipher No. 5 is as follows (mssEC 56, The Huntington Library, San Marino, California).

The key words represented the number of lines 1-20. The route is shown in the table, in which only the top and bottom rows are significant, with the two middle rows being merely for confusion to an outsider. Picking up significant figures (which represent columns, not the order) from left to right, 6, 3, 5, 7, ... (for No. 4), it indicates up the sixth, down the third, up the fifth, down the seventh, up the first, down the fourth, and down the second column.
There is no column indicators. Any columns in the table without a figure either in the top row or the bottom row are insignificant. Thus, the above example of No. 4 is for 7 columns, while that of No. 5 is for 10 columns.
The copy of Cipher No. 5 in the Friedman Collection is very similar to those in the Huntington Library but not identical in that it has a title page with "WAR DEPARTMENT CIPHER NO. 5", on the reverse side of which are given directions about the route scheme, that the pagination is printed; and that the style of dotted lines is clearly different. (Friedman harshly questions the wisdom of printing the directions when the new route scheme was designed to be obscure in case the cipher book was captured (Friedman p.41).)
The following telegram of 15 July 1863 is an example in Cipher No. 4 (Plum p.58, ASA p.72, Bates p.55, 155-157, Friedman p.40), written soon after the Battle of Gettysburg in July 1863 (Collected Works of Abraham Lincoln). (The place name is enciphered as "get ties large".)
Although this is much earlier than March 1865, when No. 4 is known to have been sent to the headquarters of Grant etc., the cipher of this despatch matches No. 4. (Although Bates says this is in No. 12, he says it is taken from Plum and his tacit correction seems to be solely because No. 12 was "effective at that time between the War Department and the Army of the Potomac.")
(Why did not Lincoln (or the cipherer presumably under his direction) use No. 12, which, according to Bates, was commonly used at the time? It is known that Cameron had left the Army of the Potomac on the 13th (Collected Works of Abraham Lincoln). So it may be natural that the cipher with the Army of the Potomac was not used.)
The key word "Blonde" indicates seven columns and eleven lines.
| (7)↓ | (2)↓ | (6)↓ | (4)↓ | |||
| Incubus[WashingtonD.C.] | Stewart[July] | Brown[15th] | Norris[18] | Knox[60] | Madison[3] | for |
| Sigh | man | Cammer | on | flea | I | wood |
| give | much | Toby | trammeled | serenade | impression | that |
| Bunyan | bear | ax | cat | children | and | awl |
| bat | since | the | knit | of | get | ties |
| large | ass | have | striven | only | to | get |
| village | skeleton | turnip | without | another | optic | hound |
| Please | tell | me | if | you | no | who |
| was | the | Harry | Madrid | locust | who | was |
| for | oppressing | bitch | quail | counsel | of | war |
| on | Tyler | Rustle | upright | Adrian | ||
| (5)↑ | (3)↑ | (1)↑ |
Taking account of phonetic spelling and code words, the following plaintext is obtained. (The last two words in the matrix are nulls to complete the rectangle.)
Apart from the above ciphers used generally, there were "department ciphers" for use with a specific department. In particular, such ciphers were used extensively in the Department of Missouri. (Plum p.59, ASA p.75)
For instance, General Pope commanding the District of North and Central Missouri in the western theater (Wikipedia), mentions a cipher "made for this department" in his despatch to G.W. Cullum, Chief of Staff, dated Syracuse, 7 December 1861 (OR, vol.8, p.412). The cipher book used in the Department of the Gulf mentioned above may be another instance. As another example, dispatch from John A. Dix to General Peck at Suffolk, dated Fort Monroe, 17 February 1863 used arbitraries "Philadelphia", "Albany", "New York", and "Georgetown" peculiar to the cipher used between these correspondents (OR, vol.18, p.540).
A cipher telegram from Maj. Gen. J.D. Cox to Brig. Gen. Robert H. Milroy, dated 3 December 1862, is in Indiana Memory Digital Collections. It begins with "China", an indicator not used in Ciphers No. 9, 10, 12, 1, and 2.
There is also another cipher telegram from G.M. Bascom to Milroy, dated 4 December 1861 here. It begins with "Turkey."
These appear to be undeciphered.
H.G. Wright (Wikipedia), commander of the Department of Ohio since August 1862, used some code or cipher such as "IX", "X I O T", "X V I" (not route transposition). It has not been identified. (OR, vol.16, p.440; vol.19, p.564; vol.20, Part II, p.259; OR, Series IV, vol.4, p.1154).
Huntington Library mssEC 40 and mssEC 37 are handwritten cipher books. They are tantalizingly similar but not the same.
The code words do not match either those of the template for No. 9, No. 10, No. 12, No. 1, No. 2 or the template for No. 3, No. 4, No. 5. Considering there were several holders (six of whom are common in both) written on the fly leaf, they were not limited to a specific department. Unlike the ciphers using the printed template, every entry has only one code word, not two. One peculiar aspect is that the numerals section encompasses fractions such as "1/8", "1/4", "3/8", etc.
The index of the first one is as follows. (The total number is roughly 70 times 22 words/page = 1540, which is close to 1608 for No. 4.)
Miscellaneous 1 to 46
Days and month 47 to 48
Numerals 49 to 50
Names of Persons 51 to 56
Corporations 57 to 65
Cities 66 to 70
The first one gives only two routes.
5 Columns: Down 5, Up 4, Down 2, Down 3, Up 1
7 Columns: Up 4, Down 1, Up 7, Down 3, Down 5, Up 6, Down 2.
The second one gives these same routes for "use on odd days of month" and gives different two routes for "even days."
More interestingly, the first one clearly explains that the route transposition is not so important as code.
This shows that, at least in some circles, it was recognized that an extensive code, as used by European diplomats or the American diplomats in the Revolutionary period (but not those during the Civil War (Gaddy p.102)), could provide the best protection of information with least complications.
Route transposition by word is not a very secure way of secret communication. Any pair of words likely to come one after another would give a clue to the transposition pattern. Later Stager ciphers relied more and more on code words ("arbitrary words") for security.
The printed template of Ciphers No. 9, No. 10, No. 12, No. 1, and No. 2 has 26*2*16=832 artibrary words (plus 48 in the TIME section). Since one line having two arbitraries are assigned to most of the entries and there are blank lines, the number of entries is about 400.
The printed template for Ciphers No. 3, No. 4, and No. 5 has 24*2+30*2*3=228 arbitary words in the time and number section (including 20 filled by hand) and 30*2*24=1440 for names and words. Since most lines having two arbitraries are now split to two entries in the latter section, the number of entries is roughly 1500 (estimated by 228/2+1400).
These are comparable to the codes used by the diplomats during the Revolutionary period, which ranged typically from 600 to 1700 entries (see my other articles).
Use of actual words or names in code in contrast the Revolutionary numerical code may be explained by the fact that the arbitrary words in the Stager cipher developed from a minor accessory to the route transposition. But it was also advantageous in being less error-prone than meaningless sequences of figures (of which at least Beckwith was aware in his contribution to No. 3, as noted below). The point does not appear to have been widely recognized in view of the confusion in the State Department after the war (see, e.g., another article).
Use of ordinary words (e.g., "shallow", "question", "squadron", "torch") as code words also had an effect of additional confusion for the outsider.
The code section of the Stager ciphers lacked means to spell words not in the list. The revolutionary codes (and many other historical codes often called nomenclators) had elemets for representing single letters or syllables. In the Civil War cipher despatches, therefore, words/names not in the list were left unencoded or represented by combination of words sounding similar to the syllables. In one instance, "Gettysburg" was encoded as "get ties large", in which at least the ending "-burg" is represented by a code word "large." In another instance, "rapidity" was represented by "rape ditty" (see another article). Such phonetic and irregular spelling are commonly used by cipher operators (see the above examples of 15 July 1863, Cipher No. 4; 19 June 1864, Cipher No. 2; 12 April 1865, Cipher No. 1 as well as another article). Although this kind of usage may avoid the weakness of the nomenclator (i.e., if the size of the code is small, an encoded text has many "spelt" portions, which may be exploited by a codebreaker), it might have posed a riddle even to an authentic recipient.
On the other hand, late Stager ciphers had entries for frequent word combinations such as "Has (or Have) arrived", "Has (or Have) been", "In front of", "in order that", etc. (No. 4).
The Confederates could never break the Federal ciphers, though they often obtained enciphered messages of the Union and sometimes published them in newspapers, calling for decipherment (Plum p.60).
Their capture of (or at least a chance to capture) Ciphers No. 6 and No. 7 in August 1862, Cipher No. 12 in July 1864, and Cipher No. 1 in September 1864 was not used to their advantage.
In 1863, E. P. Alexander, who had deciphered Union cipher before Stager, was handed a letter of 16 October 1863 in Cipher No. 9 captured from a courier but could not solve it. (Gaddy p.94-97) (Since he says he had never seen a cipher like that, he had not been informed of the captured Ciphers No. 6 and No. 7, if at all.)
He could tell it was a word transposition (which he called a "jumble"). He assumed the transposition was performed according to a predetermined random pattern block by block and expected that if the size of the block was 75 or 50 words or less, the repetition of the transposition pattern within the total of 157 words of the ciphertext would give a clue. In an attempt to find a repetition, he looked for words which might come one after another like "according to", "means of", "so that" but he could not find a repetition. Still, he noticed words "Lambs" and "ferry" would form a local place name "Lamb's Ferry" of the Tennessee River.
Route transposition ciphers employed by the Union during the Civil War might look too simple. But they did serve their purpose sufficiently given the level of their adversary (Giddy p.97).
Thomas T. Eckert Papers, The Huntington Library, San Marino, California ... providing images of original cipher books
William F. Friedman Papers, The George C. Marshall Foundation ... providing pdf of cipher books
William R. Plum, The Military Telegraph During the Civil War in the United States, vol.1 (1882) (Google), vol.2 (Internet Archive) [unless specified, vol.1 is meant herein]
David Homer Bates, Lincoln in the Telegraph Office: Recollections of the United States Military Telegraph Corps during the Civil War (1907) (Internet Archive, Google)
Army Security Agency [ASA], (ed.) Wayne G. Barker, The History of Codes and Ciphers in the United States Prior to World War I, A Cryptographic Series (1946, 1978)
W.F. Friedman, "History of Cryptology" (pdf) ... apparently corresponding to the reference in Note 2 of Gaddy below
David W. Gaddy, "Internal Struggle: The Civil War", Chapter 16 of Ralph E. Weber, Masked Dispatches: Cryptograms and Cryptology in American History: 1775-1900 3rd ed. (2013) p.88-103 (pdf)
Ali Assarpour & Kent D. Boklan (2010), "How We Broke the Union Code (148 Years Too Late)", Cryptologia, 34:3, p.200-210 ... deciphering a cipher dispatch preserved in Leigh University Digital Library (catalog entry)
David Kahn, The Codebreakers (1967)
The war of the rebellion: a compilation of the official records of the Union and Confederate armies ("OR"; unless otherwise specified, Series I is meant) (Making of America, ehistory)
The Papers of Ulysses S. Grant, Volume 10: January 1-May 31, 1864 (PUSG) (Mississippi State University Libraries, Google)
The Collected Works of Abraham Lincoln
The entire Cipher No. 9 is printed in the appendix of Plum (p.370), which has long been the only material accessible to the general public. Today, the images of original cipher books are available online.
Cipher No. 9 is preserved as Huntington Library, mssEC 67.
It is exhibited at National Cryptologic Museum.
William W. Friedman Papers has copies of Ciphers No. 9 and No. 12 (What Friedman thought to be No. 10 is actually No. 2. Instead, the copy of No. 12 is bound with an extra set of arbitrary words.).
Copies of Cipher No. 1 are preserved as Huntington Library mssEC 41, mssEC 42, mssEC 43, mssEC 44 (having an extra handwritten page before p.15), mssEC 45, mssEC 46, and a handwritten version mssEC 39.
Copies of Cipher No. 2 are preserved as Huntington Library mssEC 47 (having handwritten additional pages after p.25), mssEC 48. .
William W. Friedman Papers has copies of Ciphers No. 1 and No. 2 (the latter is labelled "10" because it lacks a title page and Friedman thought it must be No. 10.). No. 1 has a printed addenda substantially corresponding to the above extra page of mss EC 44. No. 2 has a handwritten appendix different from the extra pages of mssEC 47.
The Gilder Lehrman Institute of American History has a copy of "Cipher for telegraphic correspondence" (catalog entry). Although the present author has not seen it, the title and the handritten year "1865" suggests No. 1.
William W. Friedman Papers has copies of Ciphers No. 4, and No. 5.
Copies of Cipher No. 5 (the post-war version) are preserved as Huntington Library mssEC 49, mssEC 50, mssEC 51, mssEC 52, mssEC 53, mssEC 54, mssEC 55, mssEC 56, mssEC 57, mssEC 58, mssEC 59, mssEC 60, mssEC 61, mssEC 62, mssEC 63, mssEC 64, mssEC 65, mssEC 66.